NGINX這角色是由俄國人Игорь Сысоев於2004年創造出來的,大部分是用作負載平衡與取代Apache使用的,發音engine - x ,要裝到路由器上,這像把米格23引擎裝到BMW的感覺。俄國人真的還是有人做了。
認真的回到官方教學,有影片喔
但是我們今天不靠影片,靠自己![]()
我個人依舊喜歡維持Apache的設定檔擺置方式,也就是先創建一堆無用管理用的目錄
sudo mkdir -p /etc/nginx/sites-{available,enabled}
sudo mkdir -p /etc/nginx/modules-{available,enabled}
sudo mkdir -p /etc/nginx/conf.d
然後把設定檔塞進*-available底下,然後把決定啟用的連結到*-enabled,這作法其實對機器沒有意義,但對於人類管理很有熟悉感,而且我喜歡。
第一個編寫的
server {
listen 80 default_server;
# 從80埠聽取所有請求
server_name _;
# 全部轉去https協定去
return 301 https://$host$request_uri;
}
再來我今天要寫的是昨天給sabrina的ts109ii.myqnapcloud.com,而且只需443port部分,因為HTTP會經由剛剛設定,被301重導到這裡
# 先定義上游伺服器,就是QTS的服務頁面
upstream nas_page {
server 192.168.1.185:8080 fail_timeout=0;
}
# 直接定義 SSL部分
server {
listen 443 ssl;
ssl on;
ssl_certificate /etc/acme/ts109ii.myqnapcloud.com/fullchain.cer;
ssl_certificate_key /etc/acme/ts109ii.myqnapcloud.com/ts109ii.myqnapcloud.com.key;
#ssl_dhparam /etc/ssl/dhparam.pem;
ssl_session_timeout 5m;
ssl_protocols TLSv1.2;
ssl_ciphers "EECDH+AESGCM:EDH+AESGCM:ECDHE-RSA-AES128-GCM-SHA256:AES256+EECDH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";
ssl_prefer_server_ciphers on;
server_name ts109ii.myqnapcloud.com;
location / {
proxy_pass http://nas_page;
break;
}
}
然後把它存檔後連結到enabled底下,開始測試
sudo nginx -t && sudo nginx -s reload
然後瀏覽器就可以看到登入畫面,而且沒有被抹紅。鎖頭是安全的標示。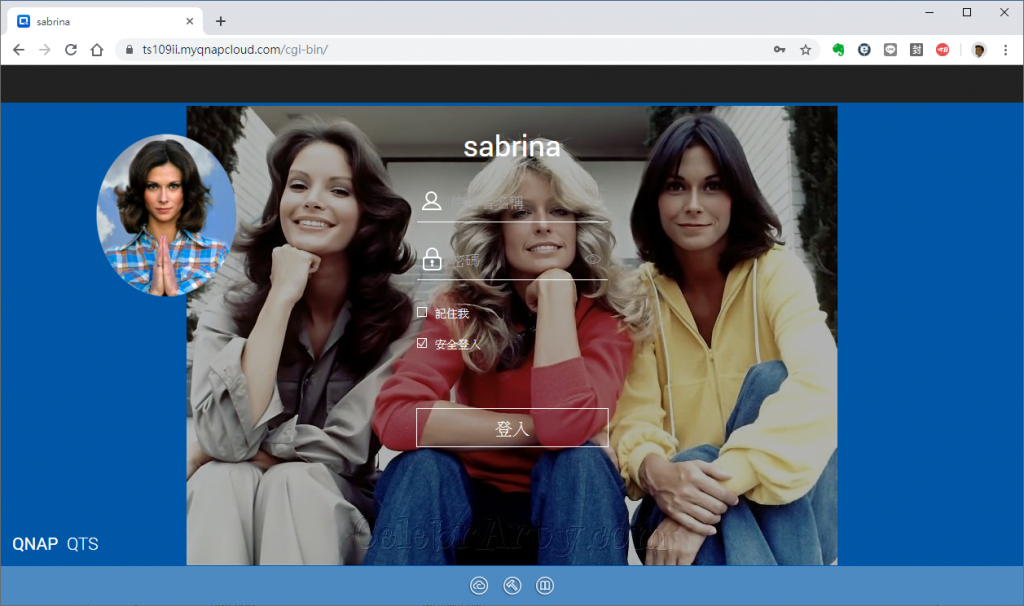
為了表示以上SSL連線等級還不錯,我們可以用工具測試
前面設定檔測出來結果是A,可以洗洗回家睡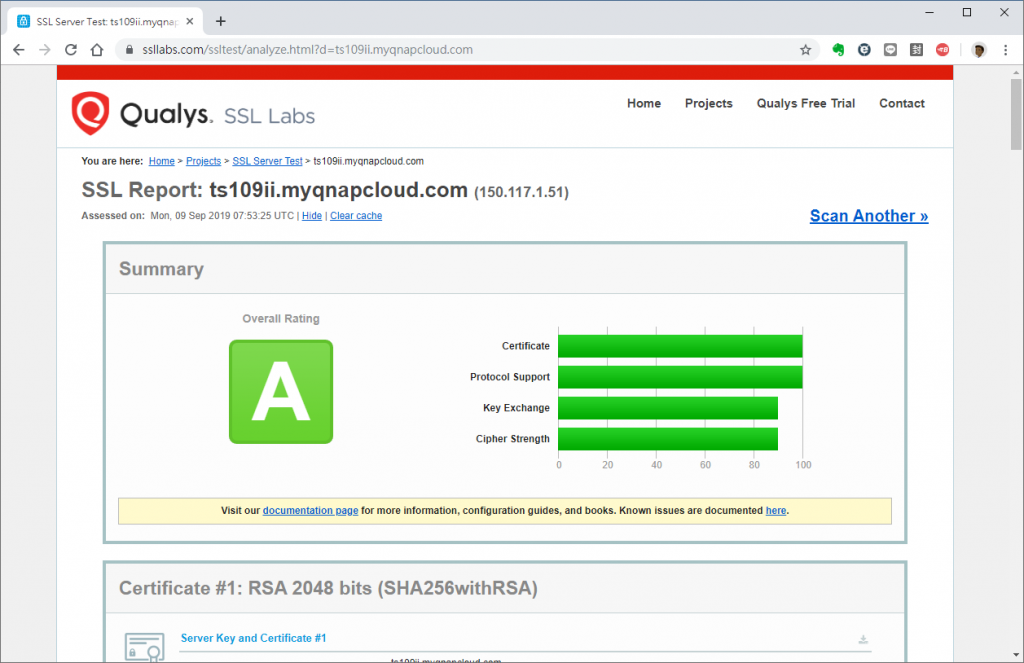
等等,只有A是沒辦法滿足我的,我要A更多![]()
用快一點的PC產生hdparam.pem
icekimo@Kelly:~$ time openssl dhparam -out dhparam.pem 2048
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
..................+..........+..............+...........................................................+.............................+.+...............................................................................+...............................................................+..............................................+.....................................................................................................................................................................................................+........+...............................................................................................+....+....+..................................+....+..........................................................+.....................................................................................................+.............................................................................................................................................................................................................................................................................................................................................................................................................................................+..................................................................................................................................+.......+................................................................................................................................................................................................................+...........................................................................................................................+.......+................................................+.......................................................................................................+.....................................+..............+.......................................................................................+..................+............................................................+....................+.........................................................................................................................................+...................................................................................................................................................................................................................................................................................+......................................+..............+........................................................................................................+........................................+..........................................................................+.......................................................+.............+.......................................................+..+...................................+.........................................................................................................................................................................+.........................................................................................................................................................................................................................................................................................+..................................++*++*++*++*
real 0m25.107s
user 0m25.102s
sys 0m0.004s
icekimo@Kelly:~$
把檔案傳到Bosley:/etc/ssl/dhparam.pem,再試試看新的設定檔
upstream nas_page {
server 192.168.1.185:8080 fail_timeout=0;
}
server {
listen 443 ssl;
ssl on;
ssl_certificate /etc/acme/ts109ii.myqnapcloud.com/fullchain.cer;
ssl_certificate_key /etc/acme/ts109ii.myqnapcloud.com/ts109ii.myqnapcloud.com.key;
ssl_dhparam /etc/ssl/dhparam.pem;
ssl_protocols TLSv1.2;
ssl_ciphers EECDH+AESGCM:EDH+AESGCM;
ssl_ecdh_curve secp384r1;
ssl_prefer_server_ciphers on;
ssl_session_timeout 10m;
ssl_session_cache shared:SSL:10m;
ssl_session_tickets off;
ssl_stapling on;
ssl_stapling_verify on;
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload";
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
server_name ts109ii.myqnapcloud.com;
location / {
proxy_pass http://nas_page;
break;
}
}
結果是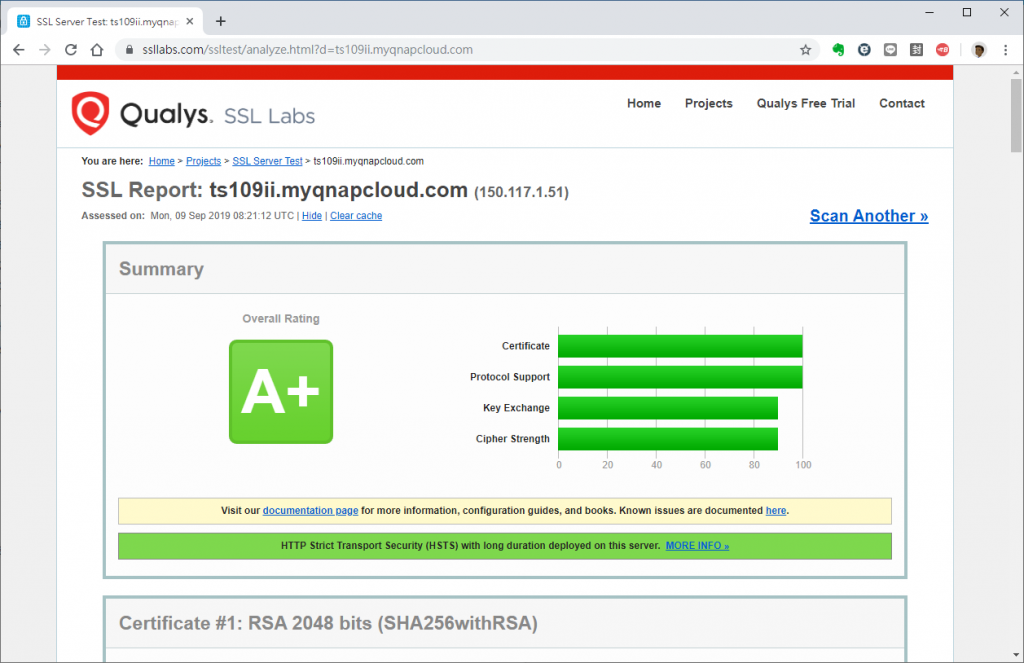
大家都看到了,現在可以安心睡覺了。
PS:為何今日不提OPKG套件?因為OpenWrt官方的Nginx是沒有SSL模組的!沒有SSL模組的!!沒有SSL模組的!!!因此請往後快轉數日,使用未來的技能「Bakery for OpenWrt」製作需要的固件重新刷機。等等,為何要重新刷機?沒有別條路嗎?
拜託,當然是不可能啊。
